Table of Contents
Overview
FVRF separates underlay and overlay networks. When using the Internet as an underlay network (Internet VPN), data on the overlay network is encrypted. IPSec encryption would then be performed between VPN gateways on the underlay network (FVRF).
In order to use VRF-aware IPSec VTI, the configuration must properly account for IPSec communication with the VPN gateway on the underlay network (FVRF).
Related articles
Please also see the following article about FVRF (Front door VRF).
Internet VPN(IPSec VPN)
Consider Internet VPNs in perspective of overlay and underlay networks.
Overlay Network : Private Network(Internal network)
Underlay Network : The Internet
Internet VPN is a technology that treats the Internet as a virtual private network. And an overlay network is a logical network built on top of an underlay network that physically transfers data. So, in Internet VPN, the overlay network is a private network (internal network). In addition, the Internet, which is where the data is actually transferred, is an underlay network.
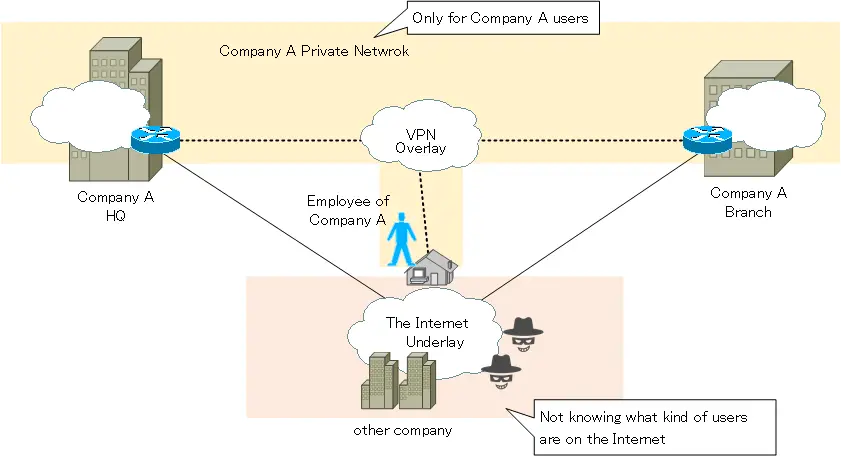
One thing to be aware of here is that the Internet is populated by users with malicious intent. There is a risk of eavesdropping and tampering when transferring overlay network data via the Internet. Therefore, the data in the overlay network is encrypted. An Internet VPN that uses IPSec for encryption is an IPSec VPN.
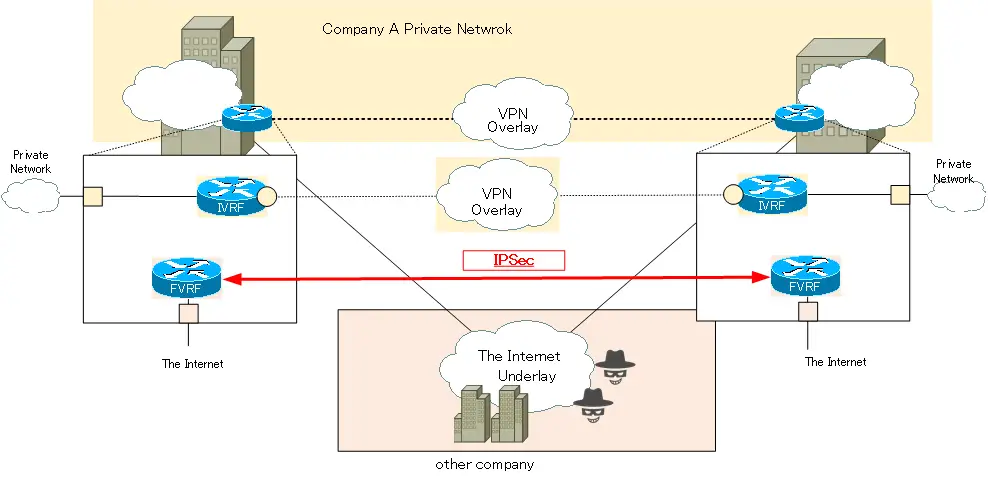
IPSec encryption on underlay network
IPSec encryption is basically performed by a VPN gateway that can communicate directly to the Internet. In other words, be properly aware that IPSec encryption is performed on underlay network. When FVRF/IVRF separates the private network (IVRF) from the Internet (FVRF), IPSec encryption is performed on FVRF.
Key Points for IPSec VTI (VRF-aware) Configuration
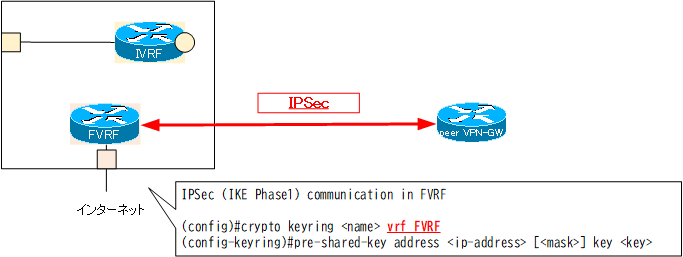
crypto keyring
The key to configuring IPSec communication in FVRF is the configuration for ISAKMP in IKE Phase 1.The ISAKMP configuration specifies the peer IPSec peer on the other side, but the default is based on the global routing table. The default global routing table does not contain any FVRF routes, so IPSec communication cannot be initiated.
IPSec peers are configured based on the FVRF routing table. To do so, specify the VRF when you specify the address of the IPSec peer in Keyring.
crypto keyring Specify VRF
(config)#crypto keyring <name> vrf <vrf-name>
(config-keyring)#pre-shared-key address <ip-address> [<mask>] key <key>
<name> : Keyring name
<vrf-name> : VRF name
<ip-address> [<mask>] : IPSec peer
<key> : Pre Shared Key
Other ISAKMP policy and IPSec transform sets and IPSec profile configurations are the same as the normal IPSec configuration. Note that for the sake of simplicity, only PSK authentication is used and ISAKMP profile configuration is not taken into account.
IPSec VTI(Vitual Tunnel Interface)
A GRE header is not specifically required for IPv4 communication between VPN gateways on a point-to-point basis. IPSec VTI reduces the overhead of the GRE header. The tunnel mode ipsec ipv4 command encrypts IPv4 packets and then directly encapsulates the IPSec ESP header and the new IP header.
The configuration commands for IPSec VTI are as follows
IPSec VTI(Virtual Tunnel Interface)
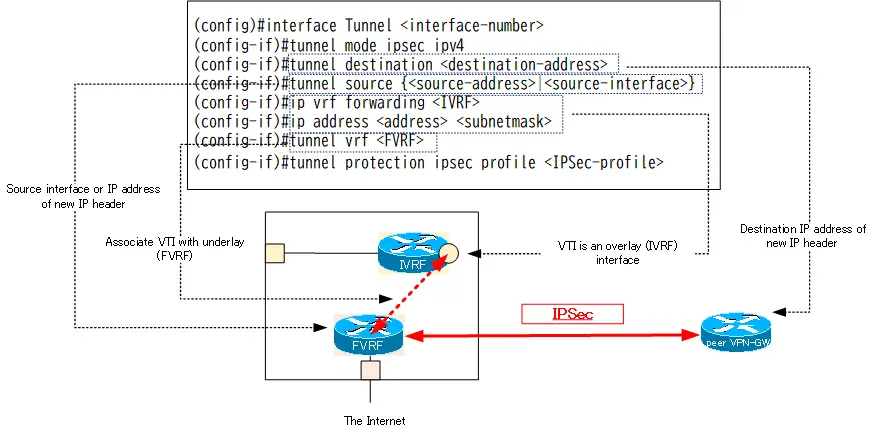
(config)#interface Tunnel <interface-number>
(config-if)#tunnel mode ipsec ipv4
(config-if)#tunnel destination <destination-address>
(config-if)#tunnel source {<source-address>|<source-interface>}
(config-if)#ip vrf forwarding <IVRF>
(config-if)#ip address <address> <subnetmask>
(config-if)#tunnel vrf <FVRF>
(config-if)#tunnel protection ipsec profile <IPSec-profile>
<interface-number> : Interface number
<destination-address> : destination IP address of new IP header
<source-address>|<source-interface> : Source address|interface of new IP header
<IVRF> : IVRF name
<address> <subnetmask> : Overlay network IP address
<FVRF> : FVRF name
<IPSec-profile> : IPSec profile name
tunnel destination and tunnel source specify the IP address or interface of the underlay network (FVRF). These will be the destination/source IP addresses of the new IP headers to be encapsulated to forward the underlay network.
The VTI itself is assigned to the overlay network (IVRF) and the IP address of the overlay network. Keep in mind that VTI is an overlay network interface.
Packets via VTI are actually forwarded in the FVRF of the underlay network, so the tunnel vrf command is used to map VTI to the FVRF. Then, associate an IPSec profile with the tunnel protection command to encrypt all packets on the Tunnel with IPSec.
Related articles
See also the following article about the tunnel vrf command.
The following is an example of IPSec VTI configuration using FVRF.
Summary
Points
- VRF-aware IPSec VPNs that use FVRF perform IPSec communications over underlay networks.
- The VPN gateway on the other side of IKE Phase 1 is configured based on the FVRF routing table by the crypto keyring command.
- IPSec VTI is an overlay network interface.
Advanced IP Routing
- Overview of Cisco Route-map
- Cisco Route-map Configuration
- GRE Tunnel Interface – Virtual Point-to-Point Connection
- GRE Tunnel Interface Configuration Example
- Overview of VRF/VRF-Lite – Virtually separating the router –
- Cisco VRF Configuration and Verification Commands
- Cisco Layer 3 VPN with VRF-Lite Configuration Example
- What Is FVRF(Front door VRF)?
- Point-to-point GRE Tunnel without FVRF
- Point-to-point GRE tunnel with FVRF (tunnel vrf command)
- IPSec VTI with FVRF
- IPSec VTI with FVRF Configuration Example
- DMVPN with FVRF
- DMVPN with FVRF Configuration Example Part1
- DMVPN with FVRF Configuration Example Part2