Table of Contents
Network ” dividing”
A router is a network device that can be used to ” divide” a network. Routers do not transmit broadcasts. Therefore, a broadcast domain, or network, can be divided by a router. Since the divided networks are interconnected by routers, communication between the divided networks is possible.
Why divide the network?
Routers can divide a network, but why do we need to divide it?
The main reasons for dividing the network are as follows
- Restrict the transfer of unnecessary data.
- Ensure security.
- Improve management efficiency
There is no clear standard on how to divide a network. We will consider the division of the network on a case-by-case basis when designing the network. For a company’s internal network, the following criteria are often used to consider the division of the network.
- Division by department or other business unit
- Division by floor or other physical arrangement
- Combination of the above
Restrict the transfer of unnecessary data
The simplest network configuration is to connect various devices to a single network consisting of only Layer 2 switches. However, this kind of network configuration will result in a lot of unnecessary data transfer. A typical example is address resolution with ARP, which is a protocol for finding a MAC address from an IP address, using broadcast.
For example, sending an ARP request to find the MAC address of a host in the immediate vicinity that is connected to the same Layer 2 switch will result in flooding everything on the same network, including other Layer 2 switches. The ARP request is completely irrelevant to hosts other than the host whose MAC address is to be queried, but it receives the ARP request, determines that it itself is not the target of the query, and discards it. This will cause extra processing on the host. In other words, a single network will also cause extra data transfer of ARP requests on the network, and extra processing load on unrelated hosts.
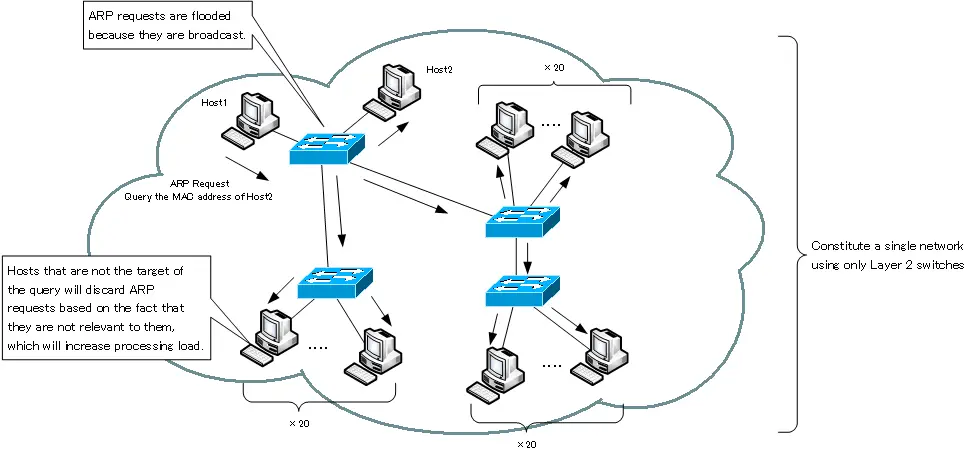
Not only broadcasts such as ARP requests, but also multicasts and Unknown unicasts are flooded, resulting in extra data transfer.
In order to reduce these extra data transfers and the associated processing load on the host, the network should be divided to an appropriate extent.
Ensure security
When a network is divided, the data between the networks always goes through a router. You can additionally check if the data transferred by the router is the data of legitimate communication. Routers act as ” barrier gates” to block unauthorized communication and ensure security.
This checking of data at the router is commonly referred to as “packet filtering”.
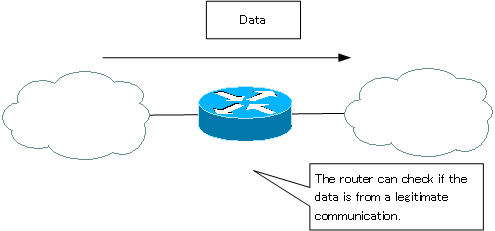
Additional configuration is required to perform security checks when forwarding on routers. Without any special configuration, as long as the destination is in the routing table, it will be forwarded; on Cisco routers, this is mainly done by configuring access control lists.
There are some enterprise layer 2 switches that can also check the data being forwarded, but they are usually not as flexible in their checking as routers.
Improve management efficiency
When a company’s internal network is configured as a single network that spans multiple locations, it can be complicated to manage. By dividing the network into appropriate areas, the scope of the network to be managed can be limited, making management more efficient.
IP Routing Basic
- Router – The central device that performs routing
- Dividing Network with router
- Layer3 Switch Overview
- Measuring the distance to the destination network -Administrative Distance and Metric
- Equal Cost Multi Path Load Balancing
- Cisco Static Route Configuration
- Example of Cisco Static Route Configuration Step by Step
- RIP Split horizon
- RIP Timers
- RIP Route Poisoning – Quickly remove unnecessary route information
- Cisco RIP Basic Configuration and Verification Commands
- Cisco RIP Configuration Example
- Generating a default route in RIP – Redistribution of static route
- Passive-Interface ~Stops Routing Protocols from Sending Packets
- Default Gateway Redundancy Overview
- How the Cisco HSRP works
- Configuring and Verifying Cisco HSRP
- How VRRP works
- Configuring and Verifying commands for VRRP [Cisco]
