Table of Contents
What is Route Poisoning?
Route poisoning is to notify the network explicitly that it is down by sending RIP route information set to metric 16. By route poisoning, network down can be detected more quickly than timer-based detection of network down, and unnecessary route information can be removed from the routing table.
One of the causes of routing loops is that unnecessary route information remains in the routing table forever. Route poisoning prevents routing loops by quickly removing unnecessary route information.
Route Poisoning is used in combination with Poison Reverse and Triggered Update. The following is a summary of the meaning of Route Poisoning, Poison Reverse, and Triggered Update.
Route Poisoning
Explicitly notify that the network is down by setting the metric 16 of the RIP route information of the downed network.
Poison Reverse
When a route poisoning is received, a poison reverse is returned. Returning a poison reverse to reliably inform that “The concerned network is not in this direction”. Poison reverse is sent even if split horizon is enabled.
Triggered update
Triggered update is to send a RIP route in response to some change besides the regular interval of the Update timer.
How Route Poisoning Works
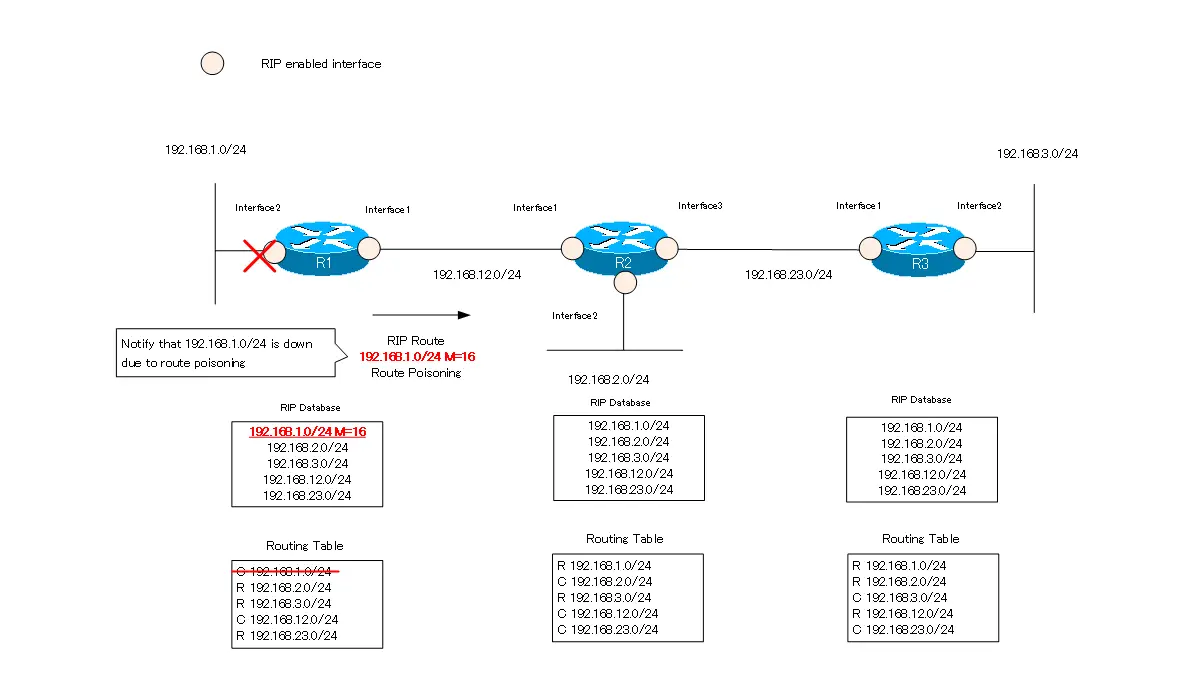
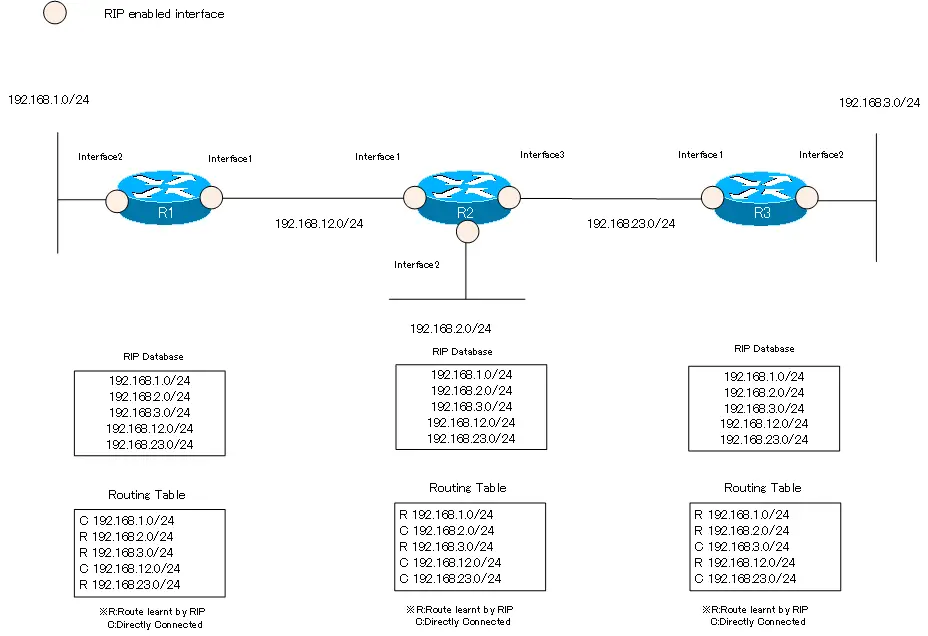
Using the following simple network diagram, we will explain how route poisoning works.
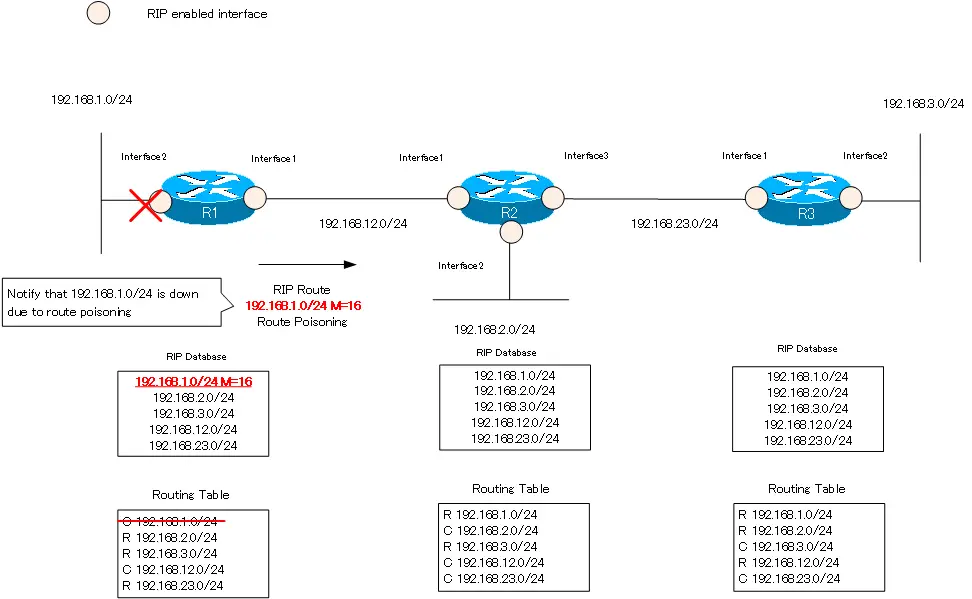
Suppose that interface 2 of R1 goes down and 192.168.1.0/24 is unreachable. R1 removes the direct connected route information “192.168.1.0/24” from its routing table. Then, it sets the metric of “192.168.1.0/24” in the RIP database to 16. R1 then sends a RIP route to R2, even if it is not at regular intervals of every 30 seconds. R1 sends RIP route “192.168.1.0/24 metric=16” to notify other routers that 192.168.1.0/24 is down.
When R2 receives the route information of route poisoning from R1, it sets the metric of the route information of “192.168.1.0/24” in the RIP database to 16. Then, remove 192.168.1.0/24 from the routing table. The RIP database “192.168.1.0/24” itself remains. R2 sends a route poisoning to R3 with a triggers update, and also returns a poison reverse to R1.
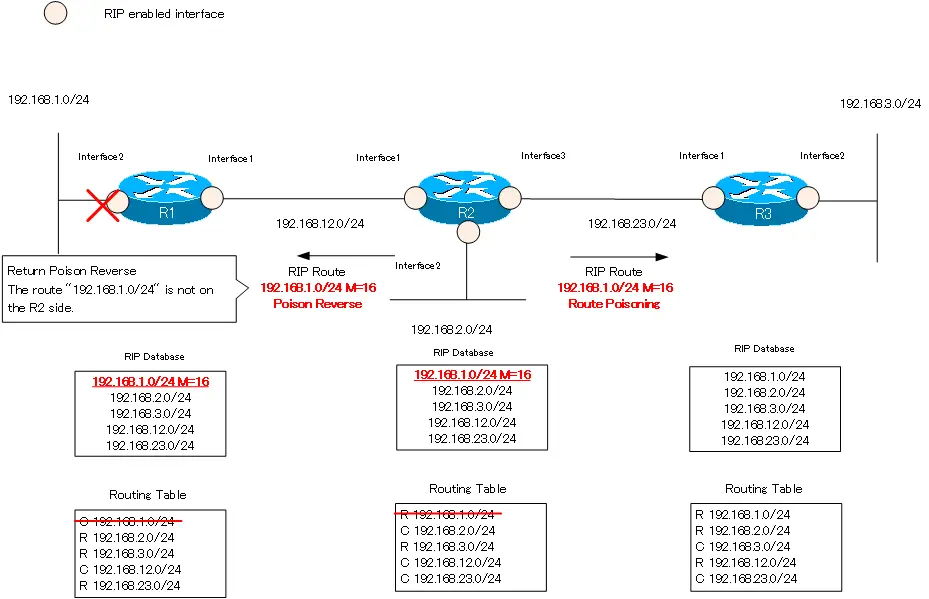
R3 works in the same way as R2. Set the metric of “192.168.1.0/24” in the RIP database to 16 and remove the RIP route “192.168.1.0/24” from the routing table. Then, send route poisoning from interface 2 with triggered update, and return poison reverse from interface 1.
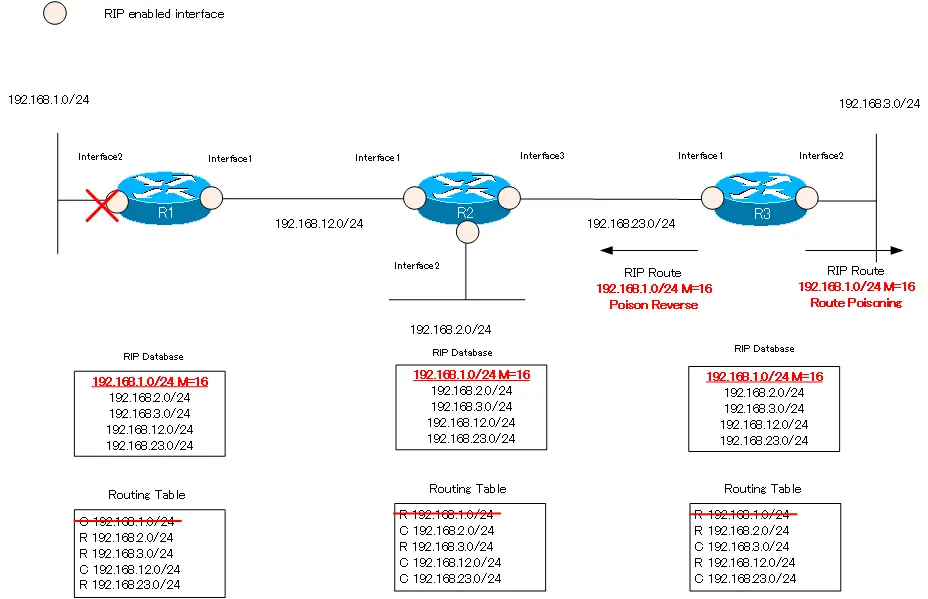
As described above, route poisoning can quickly remove unnecessary RIP route information from the routing table.
IP Routing Basic
- Router – The central device that performs routing
- Dividing Network with router
- Layer3 Switch Overview
- Measuring the distance to the destination network -Administrative Distance and Metric
- Equal Cost Multi Path Load Balancing
- Cisco Static Route Configuration
- Example of Cisco Static Route Configuration Step by Step
- RIP Split horizon
- RIP Timers
- RIP Route Poisoning – Quickly remove unnecessary route information
- Cisco RIP Basic Configuration and Verification Commands
- Cisco RIP Configuration Example
- Generating a default route in RIP – Redistribution of static route
- Passive-Interface ~Stops Routing Protocols from Sending Packets
- Default Gateway Redundancy Overview
- How the Cisco HSRP works
- Configuring and Verifying Cisco HSRP
- How VRRP works
- Configuring and Verifying commands for VRRP [Cisco]