Table of Contents
If the native VLAN configuration is mismatched…
For IEEE802.1Q trunk ports, the native VLAN configuration must match that of the opposite port. If the native VLAN configuration is mismatched, then communication for VLANs with unmatched configurations will not be possible. However, communication for VLANs that are not related to the native VLAN configuration is not a problem. Let’s consider a specific example of a native VLAN mismatch.
Related article
Please also refer to the following article about native VLAN.
Download
Click the button below to download the file for Cisco Packet Tracer, which allows you to verify the contents described in this page.
Network diagram
VLAN10, VLAN20, and VLAN30 are configured across SW1 and SW2.
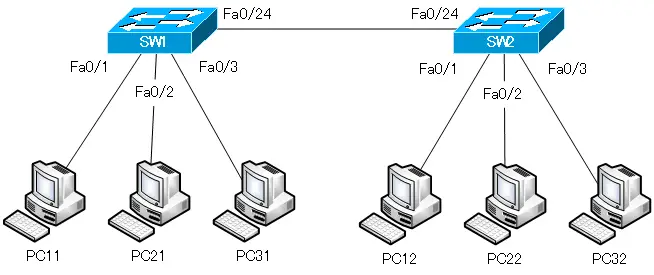
The IP address of each PC and the VLAN assignment of the port it is connected to are shown below.
| PC | Connected port | VLAN | IP address |
|---|---|---|---|
| PC11 | SW1 Fa0/1 | 10 | 192.168.10.11/24 |
| PC12 | SW2 Fa0/1 | 10 | 192.168.10.12/24 |
| PC21 | SW1 Fa0/2 | 20 | 192.168.20.21/24 |
| PC22 | SW2 Fa0/2 | 20 | 192.168.20.22/24 |
| PC31 | SW3 Fa0/3 | 30 | 192.168.30.31/24 |
| PC32 | SW3 Fa0/3 | 30 | 192.168.30.32/24 |
In addition, Fa0/24 of SW1/SW2 is configured as 802.1Q trunk port with native VLAN as VLAN10.
In normal configuration
The normal configuration of SW1 and SW2 is as follows: The configuration commands for VLANs are exactly the same for both SW1 and SW2.
SW1/SW2
vlan 10,20,30 ! interface FastEthernet0/1 switchport mode access switchport access vlan 10 ! interface FastEthernet0/2 switchport mode access switchport access vlan 20 ! interface FastEthernet0/3 switchport mode access switchport access vlan 30 ! interface FastEthernet0/24 switchport mode trunk switchport trunk native vlan 10
Related article
For more information about VLAN configuration commands in Cisco, please refer to the following article.
You can verify the VLAN configuration in detail by using the following command.
| Command | Displayed content |
|---|---|
| #show vlan brief | Verify the VLAN and port assignments. |
| #show interface trunk | Verify the trunk port. |
In SW1, the display will look like this
SW1
Sw1#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/4, Fa0/5, Fa0/6, Fa0/7
Fa0/8, Fa0/9, Fa0/10, Fa0/11
Fa0/12, Fa0/13, Fa0/14, Fa0/15
Fa0/16, Fa0/17, Fa0/18, Fa0/19
Fa0/20, Fa0/21, Fa0/22, Fa0/23
Gig0/1, Gig0/2
10 VLAN0010 active Fa0/1
20 VLAN0020 active Fa0/2
30 VLAN0030 active Fa0/3
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
Sw1#show interfaces trunk
Port Mode Encapsulation Status Native vlan
Fa0/24 on 802.1q trunking 10
Port Vlans allowed on trunk
Fa0/24 1-1005
Port Vlans allowed and active in management domain
Fa0/24 1,10,20,30
Port Vlans in spanning tree forwarding state and not pruned
Fa0/24 1,10,20,30
If the native VLANs match on SW1 and SW2, communication within VLAN 10, VLAN 20, and VLAN 30 is possible across SW1 and SW2. Pinging between the PCs in each VLAN will result in a successful response.
PC11
C:\>ping 192.168.10.12
Pinging 192.168.10.12 with 32 bytes of data:
Reply from 192.168.10.12: bytes=32 time=5ms TTL=128
Reply from 192.168.10.12: bytes=32 time=1ms TTL=128
Reply from 192.168.10.12: bytes=32 time<1ms TTL=128
Reply from 192.168.10.12: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.10.12:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 5ms, Average = 1ms
PC21
C:\>ping 192.168.20.22
Pinging 192.168.20.22 with 32 bytes of data:
Reply from 192.168.20.22: bytes=32 time<1ms TTL=128
Reply from 192.168.20.22: bytes=32 time=1ms TTL=128
Reply from 192.168.20.22: bytes=32 time<1ms TTL=128
Reply from 192.168.20.22: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.20.22:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 1ms, Average = 0ms
PC31
C:\>ping 192.168.30.32
Pinging 192.168.30.32 with 32 bytes of data:
Reply from 192.168.30.32: bytes=32 time<1ms TTL=128
Reply from 192.168.30.32: bytes=32 time<1ms TTL=128
Reply from 192.168.30.32: bytes=32 time<1ms TTL=128
Reply from 192.168.30.32: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.30.32:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
When Native VLAN configuration is mismatched
Make the native VLAN mismatch between SW1 Fa0/24 and SW2 Fa0/24. Change the native VLAN to VLAN20 on SW2 Fa0/24.
SW2
interface FastEthernet0/24 switchport trunk native vlan 20
The SW1 and SW2 show interface trunk commands indicate that the native VLAN configuration does not match anymore.
SW1
Sw1#show interfaces trunk Port Mode Encapsulation Status Native vlan Fa0/24 on 802.1q trunking 10 Port Vlans allowed on trunk Fa0/24 1-1005 Port Vlans allowed and active in management domain Fa0/24 1,10,20,30 Port Vlans in spanning tree forwarding state and not pruned Fa0/24 1,10,20,30
SW2
SW2#show interfaces trunk Port Mode Encapsulation Status Native vlan Fa0/24 on 802.1q trunking 20 Port Vlans allowed on trunk Fa0/24 1-1005 Port Vlans allowed and active in management domain Fa0/24 1,10,20,30 Port Vlans in spanning tree forwarding state and not pruned Fa0/24 1,30
Since native VLAN mismatch can be detected by CDP, the console will also display CDP error messages.
SW1
%CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on FastEthernet0/24 (10), with SW2 FastEthernet0/24 (20).
SW2
%CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on FastEthernet0/24 (20), with Sw1 FastEthernet0/24 (10).
If such native VLAN is configured in a mismatch, the mismatched VLANs cannot communicate across the switch. In this network diagram, communication within VLAN 10 across SW1 and SW2 is not possible. Also, communication within VLAN20 is not possible.
When pinging PC11 to PC12 on VLAN10, no response is returned.
PC11
C:\>ping 192.168.10.12
Pinging 192.168.10.12 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 192.168.10.12:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
A ping request (ICMP echo request) from PC11 to PC12 in VLAN 10 does not have a VLAN tag added when it is forwarded from SW1 Fa0/24, because the native VLAN in SW1 Fa0/24 is VLAN 10.
And the ping requests without VLAN tags are received by SW2 Fa0/24. Ethernet frames with no VLAN tag attached are considered to be VLAN 20, the native VLAN. Ping requests from PC11 to PC12 will not be forwarded to Fa0/1 to which PC12 is connected. This is because Fa0/1 is not a port on VLAN20. As a result, the ping will fail.
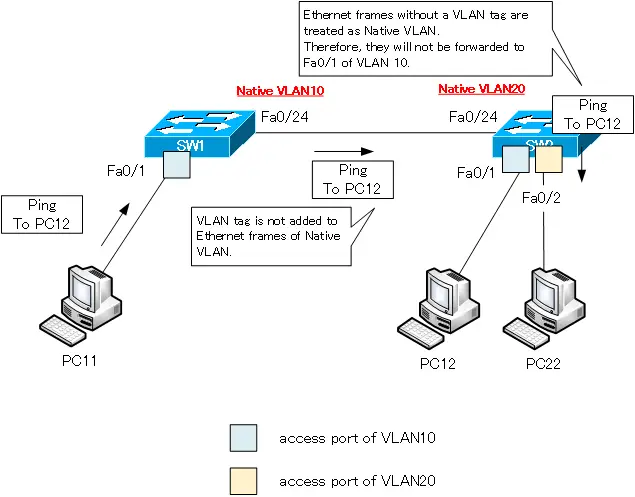
Pinging from PC21 to PC22 also fails.
PC21
C:\>ping 192.168.20.22
Pinging 192.168.20.22 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 192.168.20.22:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
Communication within VLAN 30, which is not related to the native VLAN configuration, is fine; a ping from PC31 to PC32 returns a successful response.
PC31
C:\>ping 192.168.30.32
Pinging 192.168.30.32 with 32 bytes of data:
Reply from 192.168.30.32: bytes=32 time<1ms TTL=128
Reply from 192.168.30.32: bytes=32 time<1ms TTL=128
Reply from 192.168.30.32: bytes=32 time<1ms TTL=128
Reply from 192.168.30.32: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.30.32:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
Summary
Points
- On a trunk port, the native VLAN configuration must match that of the opposite port.
- If the native VLAN is mismatched, the VLANs with unmatched configurations will not be able to communicate.
- Native VLAN configuration command on Cisco
(config-if)#switchport trunk native vlan <vlan-id>
VLAN(Virtual LAN)
- The need to divide the network
- Details of dividing the network
- VLAN Overview
- VLAN behavior
- Access port : Port assigned to only one VLAN
- Trunk port : Port assigned to multiple VLANs
- Summary of Trunk Protocols – IEEE802.1Q and ISL
- Native VLAN
- Specific example of native VLAN mismatch
- Cisco DTP
- Cisco Configuring and Verifying VLAN
- Cisco VLAN Detailed Configuration Example
- Notes on deleting VLANs
- Voice VLAN – VLAN for connecting IP phones
- VTP :Synchronize VLAN configuration
- VTP pruning – Stopping unnecessary flooding of trunk links
- Configuring and Verifying Cisco VTP
- Inter VLAN routing overview
- Inter-VLAN routing by router
- Inter-VLAN routing by Layer 3 switch
- Configuring and Verifying Inter-VLAN Routing by Cisco Router
- Cisco Configuring Inter-VLAN routing by Layer3 switch : SVI/routed port
- Cisco Layer3 Switch Basic Configuration Example
- Summary of Layer 3 Switch Port Concepts – Access Port/Trunk Port/SVI/Routed Port
- LAN Design pattern : 2-tier and 3-tier