Table of Contents
概要
DMVPNによって、拠点間のIPSec VPNの通信を動的に行うことができるように設定します。マルチポイントGREトンネル上でOSPFを利用してルーティングテーブルを作成します。そして、マルチポイントGREトンネル上の通信をIPSecで暗号化します。
関連記事
より詳しいDMVPNの設定について、以下の記事もあわせてご覧ください。
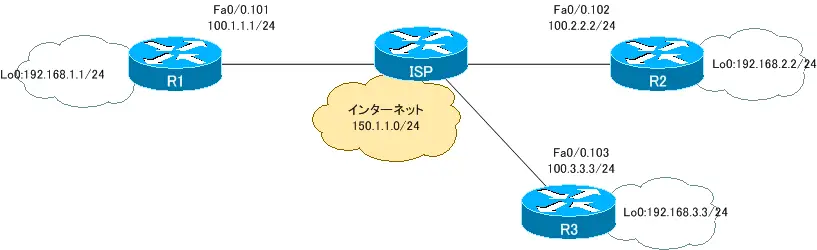
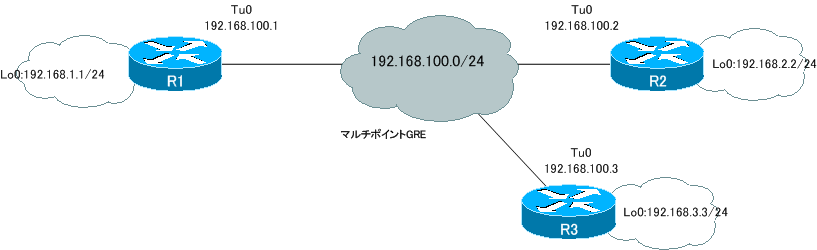
ネットワーク構成
初期設定
R1
interface Loopback0 ip address 192.168.1.1 255.255.255.0 ! interface FastEthernet0/0.101 encapsulation dot1Q 101 ip address 100.1.1.1 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 100.1.1.100
R2
interface Loopback0 ip address 192.168.2.2 255.255.255.0 ! interface FastEthernet0/0.102 encapsulation dot1Q 102 ip address 100.2.2.2 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 100.2.2.100
R3
interface Loopback0 ip address 192.168.3.3 255.255.255.0 ! interface FastEthernet0/0.102 encapsulation dot1Q 102 ip address 100.3.3.3 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 100.3.3.100
DMVPN設定
R1 DMVPN設定 NHS(Next Hop Server)
crypto isakmp policy 1 encr 3des authentication pre-share crypto isakmp key cisco address 0.0.0.0 0.0.0.0 ! crypto ipsec transform-set DMVPN_TS esp-3des esp-sha-hmac mode transport ! crypto ipsec profile DMVPN set transform-set DMVPN_TS ! interface Loopback0 ip ospf network point-to-point ! interface Tunnel0 ip address 192.168.100.1 255.255.255.0 no ip redirects ip nhrp authentication AAA ip nhrp map multicast dynamic ip nhrp network-id 1000 ip ospf network broadcast tunnel source FastEthernet0/0.101 tunnel mode gre multipoint tunnel key 1000 tunnel protection ipsec profile DMVPN ! router ospf 1 router-id 1.1.1.1 log-adjacency-changes network 192.168.0.0 0.0.255.255 area 0
R2 DMVPN設定
crypto isakmp policy 1 encr 3des authentication pre-share crypto isakmp key cisco address 0.0.0.0 0.0.0.0 ! crypto ipsec transform-set DMVPN_TS esp-3des esp-sha-hmac mode transport ! crypto ipsec profile DMVPN set transform-set DMVPN_TS ! interface Loopback0 ip ospf network point-to-point ! interface Tunnel0 ip address 192.168.100.2 255.255.255.0 no ip redirects ip nhrp authentication AAA ip nhrp map multicast 100.1.1.1 ip nhrp map 192.168.100.1 100.1.1.1 ip nhrp network-id 1000 ip nhrp nhs 192.168.100.1 ip ospf network broadcast ip ospf priority 0 tunnel source FastEthernet0/0.102 tunnel mode gre multipoint tunnel key 1000 tunnel protection ipsec profile DMVPN ! router ospf 1 router-id 2.2.2.2 log-adjacency-changes network 192.168.0.0 0.0.255.255 area 0
R3 DMVPN設定
crypto isakmp policy 1 encr 3des authentication pre-share crypto isakmp key cisco address 0.0.0.0 0.0.0.0 ! crypto ipsec transform-set DMVPN_TS esp-3des esp-sha-hmac mode transport ! crypto ipsec profile DMVPN set transform-set DMVPN_TS ! interface Loopback0 ip ospf network point-to-point ! interface Tunnel0 ip address 192.168.100.3 255.255.255.0 no ip redirects ip nhrp authentication AAA ip nhrp map multicast 100.1.1.1 ip nhrp map 192.168.100.1 100.1.1.1 ip nhrp network-id 1000 ip nhrp nhs 192.168.100.1 ip ospf network broadcast ip ospf priority 0 tunnel source FastEthernet0/0.103 tunnel mode gre multipoint tunnel key 1000 tunnel protection ipsec profile DMVPN ! router ospf 1 router-id 3.3.3.3 log-adjacency-changes network 192.168.0.0 0.0.255.255 area 0
showコマンド
【ルーティングテーブル】
R1 ルーティングテーブル
R1_DMVPN#show ip route
~省略~
Gateway of last resort is 100.1.1.100 to network 0.0.0.0
100.0.0.0/24 is subnetted, 1 subnets
C 100.1.1.0 is directly connected, FastEthernet0/0.101
C 192.168.1.0/24 is directly connected, Loopback0
O 192.168.2.0/24 [110/11112] via 192.168.100.2, 00:12:43, Tunnel0
C 192.168.100.0/24 is directly connected, Tunnel0
O 192.168.3.0/24 [110/11112] via 192.168.100.3, 00:12:43, Tunnel0
S* 0.0.0.0/0 [1/0] via 100.1.1.100
R2 ルーティングテーブル
R2_DMVPN#show ip route
~省略~
Gateway of last resort is 100.2.2.100 to network 0.0.0.0
100.0.0.0/24 is subnetted, 1 subnets
C 100.2.2.0 is directly connected, FastEthernet0/0.102
O 192.168.1.0/24 [110/11112] via 192.168.100.1, 00:12:59, Tunnel0
C 192.168.2.0/24 is directly connected, Loopback0
C 192.168.100.0/24 is directly connected, Tunnel0
O 192.168.3.0/24 [110/11112] via 192.168.100.3, 00:12:59, Tunnel0
S* 0.0.0.0/0 [1/0] via 100.2.2.100
R3 ルーティングテーブル
R3_DMVPN#show ip route
~省略~
Gateway of last resort is 100.3.3.100 to network 0.0.0.0
100.0.0.0/24 is subnetted, 1 subnets
C 100.3.3.0 is directly connected, FastEthernet0/0.103
O 192.168.1.0/24 [110/11112] via 192.168.100.1, 00:15:48, Tunnel0
O 192.168.2.0/24 [110/11112] via 192.168.100.2, 00:15:48, Tunnel0
C 192.168.100.0/24 is directly connected, Tunnel0
C 192.168.3.0/24 is directly connected, Loopback0
S* 0.0.0.0/0 [1/0] via 100.3.3.100
【NHRPキャッシュ】
R1 NHRPキャッシュ(NHS)
R1_DMVPN#show ip nhrp detail 192.168.100.2/32 via 192.168.100.2, Tunnel0 created 02:15:45, expire 01:46:48 Type: dynamic, Flags: authoritative unique registered NBMA address: 100.2.2.2 192.168.100.3/32 via 192.168.100.3, Tunnel0 created 02:15:42, expire 01:47:10 Type: dynamic, Flags: authoritative unique registered NBMA address: 100.3.3.3
R2 NHRPキャッシュ
R2_DMVPN#show ip nhrp detail 192.168.100.1/32 via 192.168.100.1, Tunnel0 created 02:20:38, never expire Type: static, Flags: authoritative used NBMA address: 100.1.1.1
R3 NHRPキャッシュ
R3_DMVPN#show ip nhrp detail 192.168.100.1/32 via 192.168.100.1, Tunnel0 created 02:21:14, never expire Type: static, Flags: authoritative used NBMA address: 100.1.1.1
【IPSec SA】
R1 IPSec SA
R1_DMVPN#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 100.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (100.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.2.2.2/255.255.255.255/47/0)
current_peer 100.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 152, #pkts encrypt: 152, #pkts digest: 152
#pkts decaps: 148, #pkts decrypt: 148, #pkts verify: 148
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 3, #recv errors 0
local crypto endpt.: 100.1.1.1, remote crypto endpt.: 100.2.2.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0.101
current outbound spi: 0x2B8DE8E(45670030)
inbound esp sas:
spi: 0x41AF28EB(1101998315)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2004, flow_id: SW:4, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4472051/2263)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x2B8DE8E(45670030)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2001, flow_id: SW:1, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4472050/2263)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (100.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.3.3.3/255.255.255.255/47/0)
current_peer 100.3.3.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 149, #pkts encrypt: 149, #pkts digest: 149
#pkts decaps: 147, #pkts decrypt: 147, #pkts verify: 147
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 8, #recv errors 0
local crypto endpt.: 100.1.1.1, remote crypto endpt.: 100.3.3.3
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0.101
current outbound spi: 0x1FD2441F(533873695)
inbound esp sas:
spi: 0x1DDD9421(501060641)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2002, flow_id: SW:2, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4533275/2286)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x1FD2441F(533873695)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2003, flow_id: SW:3, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4533274/2286)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R2 IPSec SA
R2_DMVPN#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 100.2.2.2
protected vrf: (none)
local ident (addr/mask/prot/port): (100.2.2.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.1.1.1/255.255.255.255/47/0)
current_peer 100.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 7, #pkts encrypt: 7, #pkts digest: 7
#pkts decaps: 7, #pkts decrypt: 7, #pkts verify: 7
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 100.2.2.2, remote crypto endpt.: 100.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0.102
current outbound spi: 0x2A3C192(44286354)
inbound esp sas:
spi: 0x63B72CEF(1672948975)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2001, flow_id: SW:1, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4558452/3530)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x2A3C192(44286354)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2003, flow_id: SW:3, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4558452/3530)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R3 IPSec SA
R3_DMVPN#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 100.3.3.3
protected vrf: (none)
local ident (addr/mask/prot/port): (100.3.3.3/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.1.1.1/255.255.255.255/47/0)
current_peer 100.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 164, #pkts encrypt: 164, #pkts digest: 164
#pkts decaps: 167, #pkts decrypt: 167, #pkts verify: 167
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 100.3.3.3, remote crypto endpt.: 100.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0.103
current outbound spi: 0x1DDD9421(501060641)
inbound esp sas:
spi: 0x1FD2441F(533873695)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2002, flow_id: SW:2, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4557703/2115)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x1DDD9421(501060641)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2001, flow_id: SW:1, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4557703/2115)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
インターネットVPN
- インターネットVPNの概要
- インターネットへの接続形態
- VPNサービスとは?
- NordVPN ~セキュアなVPNサービスを手軽に利用しよう~
- IPSecの概要
- IKE ~SAの生成と管理~
- IPSec サイト間VPNの動作
- IPSec サイト間VPNの設定 ~crypto mapによる設定~
- IPSec サイト間VPNの設定例
- [演習]サイトツーサイトIPSec-VPN(crypto map)
- [演習]サイトツーサイトIPSec-VPN(VTI)
- [演習]サイトツーサイトIPSec-VPN(VTI) トラブルシューティング
- IPSec 設定ミスの切り分けと修正 Part1
- IPSec 設定ミスの切り分けと修正 Part2
- IPSec 設定ミスの切り分けと修正 Part3
- DMVPNの設定例
- DMVPN設定演習[Cisco] NHRP Phase1
- DMVPN設定演習[Cisco] NHRP Phase2
- DMVPN設定演習[Cisco] NHRP Phase3
- SSL-VPNの実現方式
- SSL-VPN(クライアントレス)の設定例 (Cisco)